Summary of NFC Secure Data Storage Using Atmega644
The project implements secure storage of sensitive data using Shamir's secret sharing algorithm distributed among multiple agents via Near-field Communication (NFC). It allows encoding a secret key split among agents requiring a threshold to reconstruct it or alternatively encrypting data with AES stored on a single NFC card. The system uses an ATmega1284 microcontroller interfacing with a PN532 NFC shield, keypad, and television display, managing concurrent processes and complying with NFC standards to ensure secure card read/write operations.
Parts used in the NFC Secure Data Storage Using Atmega644:
- PN532/RFID Controller Shield for Arduino + Extras
- 36-pin 0.1" header strip
- MiFare Classic 1K Card
- 16-Button Hexadecimal Keypad
- Mega1284 Microcontroller
- White Board
- Television
- Header socket/plug (x6)
- Power Supply (x2)
- Cable Clamp (x2)
- MiFare Classic 1K Cards
Summary
“Enabling secure storage capabilities for sensitive data through standardized methods of encryption or multiple agent distribution.”
Our group chose to implement a secure form of storage for sensitive information such as passwords or identification numbers. This is modeled after Shamirs secret sharing algorithm. It allows us to distribute information regarding the secret key among several agents. In this way, you would need a certain minimum threshold number of agents to collaborate to generate the secret key. With this base concept down, we needed a way to physically store and distribute this information. We decided to use Near-field communication (NFC) as the medium through which to transfer information. NFC builds on top of RFID and was chosen for both its limited range and versatility. Our current implementation stores information on NFC cards, but future enhancements can allow communication with other devices such as NFC-enabled phones. For demonstration purposes, we combined both the encoder and decoder into one device. The user can specify the number of agents and the threshold number to encode a certain key. The other option is to use the Advanced Encryption Standard (AES) to encrypt the data and store it on a single card. The user is able to choose either option and interact with the device through a keypad and a television screen.
High Level Design
Rational and Inspiration Sources
There are many situations in which security is of great concern. One such example is gaining access to a restricted area. If the key requires a certain number of people present to decode it then you guarantee that no one person is alone in the restricted area. Similarly, if one is trying to move account numbers, encryption keys or even nuclear launch codes, you do not need to place the full burden of one person carrying the key; but instead, it can be split with several people. In this way, if any individual pieces are intercepted, there is not enough information to regenerate the key. By using NFC, there is great versatility in how the information can be stored. There are NFC cards, tags, stickers and phones widely available in today�s market. Its low range protects data from being intercepted by a third party in the distance. Additionally, for different types of data that are typically written to and read from tags, the transfer speed gets it done very quickly.
Hardware & Software Tradeoffs
In an attempt to reduce the amount of inputs coming into the MCU at once, we moved a lot of the controls for switching states from hardware to software. Instead of using more pushbuttons, we made our user interface more content-aware to detect valid and invalid inputs in order to cycle through the various states of the menus. We minimized the inputs to keypad entry and NFC card scanning in order to accomplish this goal. However, this increased the amount of overhead written into the program to handle the decisions in software. It then became a goal to optimize the program in order to handle the speed and timing constraints that each component required.
Applicable Standards
Our design complies with the NFC standard ISO/IEC 14443 A, which is the standard for interacting with contactless cards. The MiFare card complies with the mutual three pass authentication method as defined by ISO/IEC 9798-2 and is implemented in our pn532_spi.c library. The PN532 NFC Shield itself complies with the air transmission standard ISO/IEC 18092.
Hardware and Software Design
Program Details
The main program consisted of a large state-machine whose states controlled the television display and controlled the user�s different actions, such as encoding and decoding information to/from the NFC cards. The main difficulties in our program involved both being able to interact with components through NFC as well as getting all of the timing down on one processor in order to scan the keypad, run the television display, and read/write to NFC cards through SPI. The first obstacle was writing the library for interacting with the PN532 chip on the NFC shield. This component was not only designed to run on Arduino with its Sketch language, but the library provided by Adafruit was also in C++. This meant we had to write our own library in C to interface with the ATmega1284. The C++ library served as a useful guide when doing so.
Structure of the PN532 SPI Library
At its lowest level, the library has the basic read/write SPI functions. This served as the foundation from which to build the rest. The mid-level SPI code contained functions to send the write command to the NFC shield, read raw data, and read the SPI status. The high-level SPI code contains a SPI read with acknowledgment function. We took these functions and used them as tools to build functions that operated on a higher level that fulfilled more common functions. The sendCommandCheckAck was used in several places in the library as it allowed us synchronize the card and the antenna to begin read/write operations. The readPassiveTargetId function reads the unique identification number of the card, written by the manufacturer. Each number is unique not only to the manufacturer but also to any other card. Next are the readMemoryBlock and writeMemoryBlock functions that write information to a given block in the card. However, writing to a card is not as simple as sending information. The ISO 14443 type-A standard has certain procedures to be followed in order to write to the card. Specifically, type-A requires that a block be authenticated before it is read or written, which is what the function authenticateBlock does. The authentication procedure is what provides so much security in these NFC communications.
Concurrency Issues
There are four main processes that are supposed to run concurrently. The NFC shield is running continually, waiting for a card to read/write and communicates through SPI. The television requires a constant rate of pixel blasting in order to maintain an image. The MCU is constantly scanning the keypad, awaiting user entry. Lastly, we have our main program that interprets and synthesizes all the inputs that it is receiving at once. We had to use many of the tricks we learned in the digital oscilloscope lab in order to get all of these to run without colliding. The television provided the largest overhead, followed by the NFC shield, the keypad, and the main program. They were thus prioritized in that order to work out the timing. In the end, our program proved to be too fast to the point where we had to introduce delays in order to maintain the correct timing among the state machine. This greatly exceeded our expectations and became advantageous when implementing the rest of the program.
Hardware Details
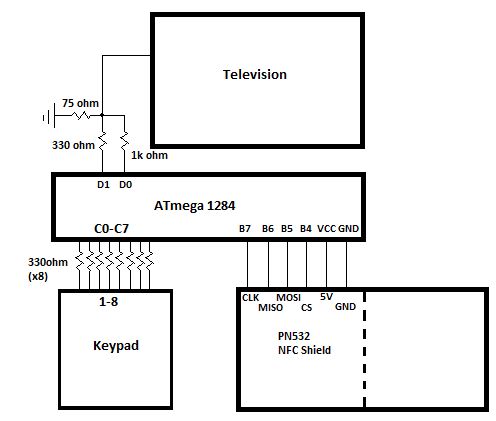
The MCU used was the ATmega1284. A 16-button keypad with pins 0-8 was connected to pins C0-C7, respectively with a 330ohm resistor at every pin. The NFC shield was the PN532 NFC Shield from Adafruit Industries. A solder bridge over SEL0 and SEL1 was used in order to set it to communicate through SPI. The clock, MISO, MOSI, and chip select pins were connected to pins B7, B6, B5, and B4, respectively. This particular shield can function at either 3.3V or 5V, so the VCC connection was connected to the +5V pin. Lastly, the television sync was connected to pin D0 and the video to pin D1.
Refer to Figure 5 in Appendix B for a diagram of the connections. We were originally working with the ATmega644, but reverted back to the ATmega1284 for the USART functionality, which was crucial to both constructing and debugging the system. As for NFC, we also had a few Maxim cards which were of type-B, different from the MIFARE which is type-A. The difference between these two types completely changes the way we write to them. There are different security protocols and after reading through a few data sheets, we decided against it for the sake of time.
parts List:
| roduct Name | Vendor | Part # | Price |
|---|---|---|---|
| PN532/RFID Controller Shield for Arduino + Extras | Adafruit | 789 | $39.95 |
| 36-pin 0.1″ header strip | |||
| MiFare Classic 1K Card | |||
| 16-Button Hexadecimal Keypad | n/a | n/a | $6 |
| Mega1284 Microcontroller | Atmel | n/a | $5 |
| White Board | n/a | n/a | $6 |
| Television | n/a | n/a | $18 |
| Header socket/plug (x6) | n/a | n/a | $0.30 |
| Power Supply (x2) | n/a | n/a | $10 |
| Cable Clamp (x2) | n/a | n/a | $2 |
| MiFare Classic 1K Cards | n/a | n/a | $11.85 |
| Total | $99.10 | ||
For more detail: NFC Secure Data Storage Using Atmega644