Introduction and Rationale
We used our ECE 4760 final project as a platform to develop a proof of concept for Mivo. Mivo is a low-cost, stripped down mobile payment system. Our prototype combines Radio Frequency Identification (RFID), Security Pin Authentication and Ethernet Data Transfer to provide a prototype for a low-cost secure payment system that has the potential to change lives in rural areas of developing countries.
The Idea:
Mivo is a service that aims to securely and conveniently move retail banking and financial services to cell-phones. It is a mobile-banking facility for the unbanked. We propose to deliver access to financial services to the unbanked, on low-end mobile phones. Worldwide there are 4.1 billion cell-phone users compared to just 1.6 billion people with bank accounts; further, research reveals a potential of $250 billion in micro-finance in the world, yet only $25 billion has been lent out. Mivo has the potential to bridge both gaps.
This is an idea targeted at developing countries; as the Internet and ATMs are unavailable in rural areas and penetration is low even in urban areas there are many problems faced (including access to financial services and remittances). The idea is to construct a complete mobile-payment ecosystem comprised of RFID-enabled phones and text message (SMS) transactions to access a virtual account- a simple, fast and safe solution for financial transactions. While Mivo can be a life-changer in the developing world, it also has awesome applications in the developed world. As an example application, Mivo users would be able to pay for an airline or movie ticket by text-messaging an advertised SMS code and then skip the line at the counter by scanning their RFID-equipped phone at the entry point and entering their authentication details.
High Level Design
We envisioned that the tasks of a generic technological payment system are:
- Identification
- Authentication
- Database access and update
Identification:
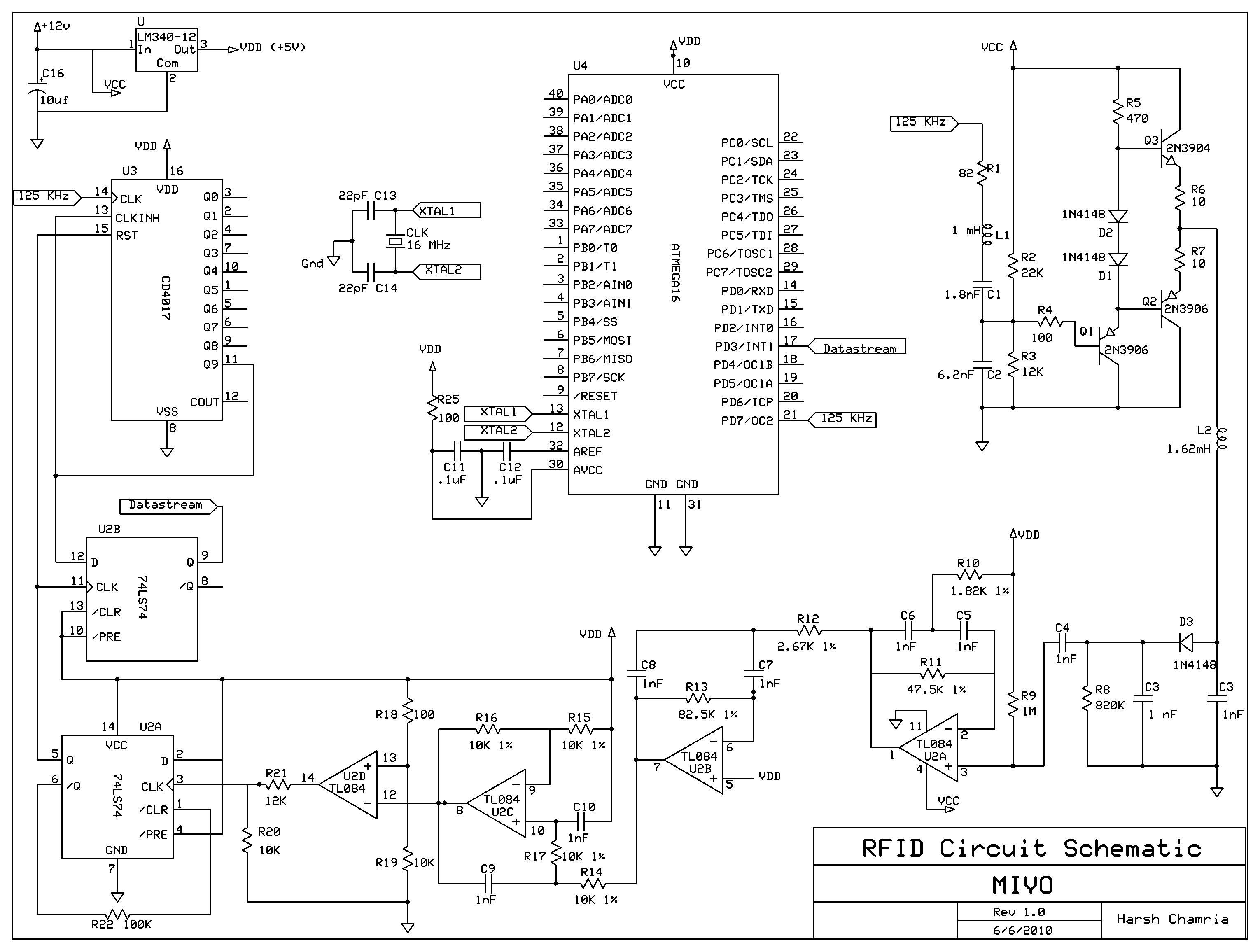
After considerable contemplation and debate we decided that we would use RFID (Radio Frequency Identification) for Identification. We selected RFID because this standard has a fairly short-range connection, a small connection-setup time (both of which make it slightly tougher to hack than some other standards) and also because we knew that our Cornell Cards have RFID tags embedded within them. Thus, we would be able to use these cards for identification instead of investing in RFID tags.
Authentication:
We decided to use 4-digit security pin for Authentication because we wanted a system that is quick and convenient while being secure. We had also considered adding a Fingerprint based authentication; however, due to the time constraint of 5 weeks we decided that we would add this feature later.
Database access and update:
Now for the Database access, while we would eventually want to transfer data over airwaves (in order to exploit the existing telecommunication infrastructure and avoid the hassle of setting up Ethernet connections), for the purpose of this project we decided to use Ethernet based data transfer. We took this decision because neither of us is familiar with 2G or 3G standards and implementing this in 5 weeks would have been a stretch.
Going into this project we were both really apprehensive of how much we would be able to achieve, but as advised by Professor Bruce Land and our TA Yuchen Zhang, we divided up our (Goliath-of-a-) project into sub-tasks. Neither of us has taken a course on RFID design; however we researched online to find a host of resources to help us on our circuit and data-analysis. In fact we found the documentation on Proximity Security System (project by Craig Ross and Ricardo Goto, Spring 2006) extremely helpful in selecting our design methodology. Their page also linked us to [Jonathan Westhues Proximity website] and the [microID 125kHz RFID System Guide] which provide some solid documentation on designing secure proximity systems. We had used the LCD and keypad in previous labs and hence we referred to Prof. Lands code: LCD and keypad. Eventually after many hours of research we were lucky to come across Brian Bryces website (please refer to the Acknowledgements section) which served as a good reference for us while we were designing our Ethernet system. We decided to use the Atmel Mega 16 microcontroller (as opposed to the Mega 644 that we had used in all of our labs during the semester) simply because we did not need much on-chip memory and the Mega 16 would count as a free chip in our budget (of course, we were also comfortably under-budget).
Overview:
At the top-level, we wrote a state machine that controls the working of the entire system and integrates the various subsystems into a single entity. We will go into the details of the state machine later in the Logical Structure section of our report. However, it is important to understand the top level working of the system. After the cashier enters the amount using the 4×4 keypad the state machine transitions to the RFIDInput state, which triggers the RFID system. Our system uses an inductive-antenna coil to activate the RFID tag in our Cornell ID cards and then reads off the response from the card. This response is put through a bandpass filter and wave rectification filter and finally some digital logic (more on this in the RFID section of our report) before it is fed to the Atmel Mega16 microcontroller, which further decodes the data to extract a unique code that is consistent across multiple tries for each RFID tag. Then the user is prompted to enter his/her security pin. This data and the user entered security-pin are transferred to an Ethernet Controller (connected using an SPI interface) which accesses a mySQL database through an Ethernet connection (for the detailed implementation please look at the Ethernet section of our report). A program at the backend server replies with a Good G, or Bad B message. All the user-prompts and data output are displayed on a 16×2 LCD screen and all input (at Point of Sale, i.e. front-end) is through a 4×4 keypad.
Logical Structure
A state machine controls how the entire system works. We decided to use this topology because we were going to use a state machine (from Bruces keypad code) to debounce a button-press on the keypad and extending this structure to control the various sub-systems of our project seemed a logical next step.
Our program starts up in the NoPush state. If a key is pressed it moves to the Debounce state (which occurs after an interval of time equal to debounce_interval set to 30 milliseconds). We used a 4×4 keypad and we had to debounce the keypad because electrical contacts in mechanical pushbutton switches often break contact multiple times when the button is first pushed. The debouncing logic removes the resulting ripple signal, and provides a clean transition. The idea here is that the bouncing of the switch will stop after an interval of 30 milliseconds.
Parts List:
| Part | Manufacturer/ Supplier | DigiKey Part Number | Unit Cost | Quantity | Total |
|---|---|---|---|---|---|
| RF Choke | JW Miller A Bourns Company | 5800-102-RC | $1.33 | 1 | $1.33 |
| Op Amp | Texas Instruments | TL084CN | $0.63 | 1 | $0.63 |
| Decade Counter | Texas Instruments | CD4017BE | $0.50 | 1 | $0.50 |
| Dual D Flip Flop | ECE 4760 Lab | SN74HC74N | $0.00 | 1 | $0.00 |
| Diodes | ECE 4760 Lab | 1N4001 | $0.00 | 1 | $0.00 |
| Transistors | ECE 4760 Lab | 2N3906. 2N3904 | $0.00 | 2 | $0.00 |
| Ethernet Controller | WIZNET | WIZ812MJ | $0.00 | 1 | $0.00 |
| LCD | ECE 4760 Lab | – | $8.00 | 1 | $8.00 |
| Keypad | ECE 4760 Lab | – | $6.00 | 1 | $6.00 |
| Breadoard | ECE 4760 Lab | – | $6.00 | 1 | $6.00 |
| Power Supply | ECE 4760 Lab | – | $5.00 | 1 | $5.00 |
| Custom PC Board | ECE 4760 Lab | – | $4.00 | 1 | $4.00 |
| Mega16 | ECE 4760 Lab | – | $0.00 | 1 | $0.00 |
| DIP sockets | ECE 4760 Lab | – | $0.50 | 2 | $1.00 |
| Header Pins | ECE 4760 Lab | – | $0.05 | 60 | $3.00 |
| Misc: Caps/ Resistors/ Regulators | ECE 4760 Lab | – | $0.00 | 1 | $0.00 |
| Total | $35.46 |
For more detail: RFID based Mobile Payment System Using Atmega644