Description
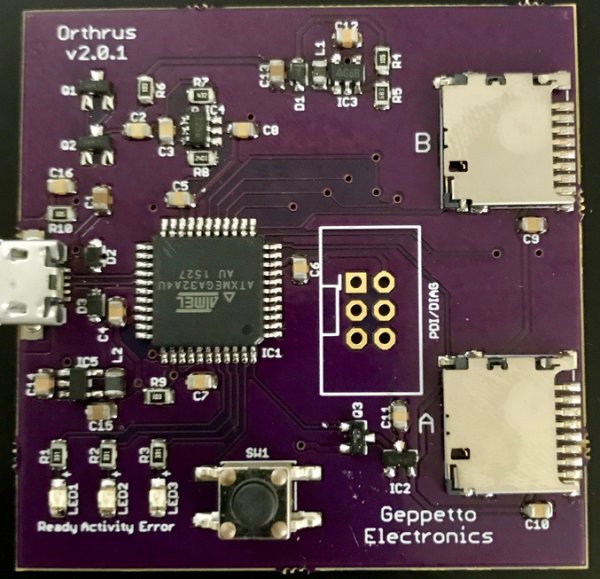
This allows you to securely transport a data set by writing it onto a pair of cards and separately transporting them to a destination for recombination.
The intent is that only the pairing of two cards becomes in any way special. A card pair could be inserted in any Orthrus device and the data would be made available. But with only one card, all you get is half of the data encrypted with a key which you only half-possess.
I’d like to express my gratitude to Dean Camera of the LUFA project.
Details
The first block of each card is reserved as a key storage block. The size of the volume reported to the USB host is determined by taking the smaller of the two card sizes, subtracting one and doubling that. The first block on each card contains a structure with the following:
- A magic constant compiled into the firmware to identify the card as belonging to an Orthrus volume.
- A flag bit identifying the card as either the “A” or “B” card (the cards can be inserted in either order and it should still work).
- A 64 byte volume ID.
- A 32 byte card key value.
- A 16 byte nonce value for the block tweaking (of which 12 bytes are used).
When the device is initialized (either when its inserted into a host with two cards already installed or when the second card is inserted), each of the key blocks is checked. If the magic value is wrong, or if the two volume ID values don’t match or if there isn’t one “A” and one “B” card, then the error light is turned on and the volume isn’t mounted. This prevents cards inserted mistakenly from being corrupted. To bootstrap, there’s a button on the board. If the button is pushed while the error light is on, then the two key blocks are initialized and the device made ready.
If the pre-initialization checks succeed, then the two card key values are shuffled together (in “A” “B” order) to make a 64 byte buffer. The two halves of this shuffled data is fed through AES CMAC with an all-zero key, with the two results concatenated together. The result of that becomes the new AES key and the CMAC is run over the two halves of the volume ID, again, with the two results concatenated together. The result of that becomes the AES key for the volume. At that point, the drive is ready.
Read more: Orthrus – SD card secure RAID USB storage
